Redis doesn't ship with TLS support out of the box, a heinous omission to be sure. TLS support can be enabled by compiling a custom build yourself, but the official "Securing Redis" guide recommends to use a secure network tunnel between the client and server instead. The guide gives spiped as an example of such a tunneling software, but we didn't want to use spiped because, as j3s said,
honestly spiped seems cludgy and has an ambiguous license
So, we decided to make our own, because we could leverage unix sockets (and therefore, unix permissions) on both sides to make it as secure as possible and eliminate credentials sent over unsecured TCP (including unsecured TCP on localhost) entirely.
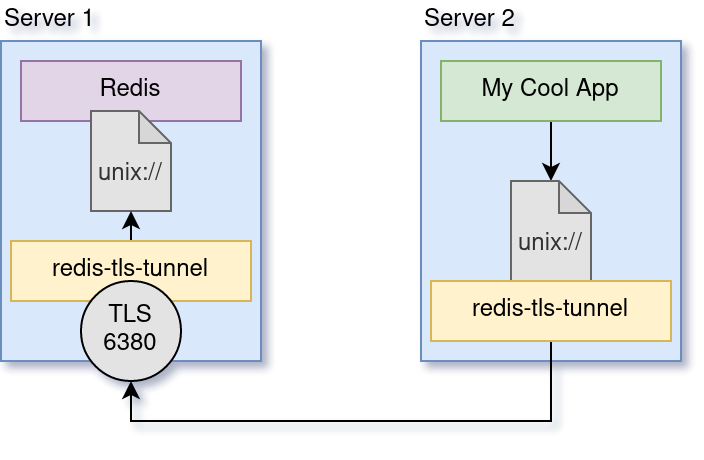
Technically this would work for any program that uses a Unix socket, but redis is the only one we know of that supports unix sockets while not supporting TLS. That's the only real reason this thing is named after / associated with redis.
Check it out!
--> https://giit.cyberia.club/~forest/redis-tls-tunnel <--
j3s is also looking into creating an alpine linux package for it, so stay tuned for that.

Comments